-
simplified Chinese character -
Simplified Chinese English
Shangpin China Joins Hands with Beisheng Internet to Create a New Chapter in Website Construction
Security Control of Beijing University Website Construction Cluster System
-
Access control and permission management: Ensure that only authorized users can access the management interface and resources of the website cluster. -
Implement a strong password policy and encourage the use of multifactor authentication. -
Set different permissions for different user roles to limit their access and operation scope.
-
-
Network firewall and intrusion detection system: Set network firewall and intrusion detection system outside and inside the cluster system to monitor and prevent malicious attacks. -
Configure firewall rules to limit unnecessary network traffic. -
Implement real-time intrusion detection to detect and respond to abnormal activities in a timely manner. 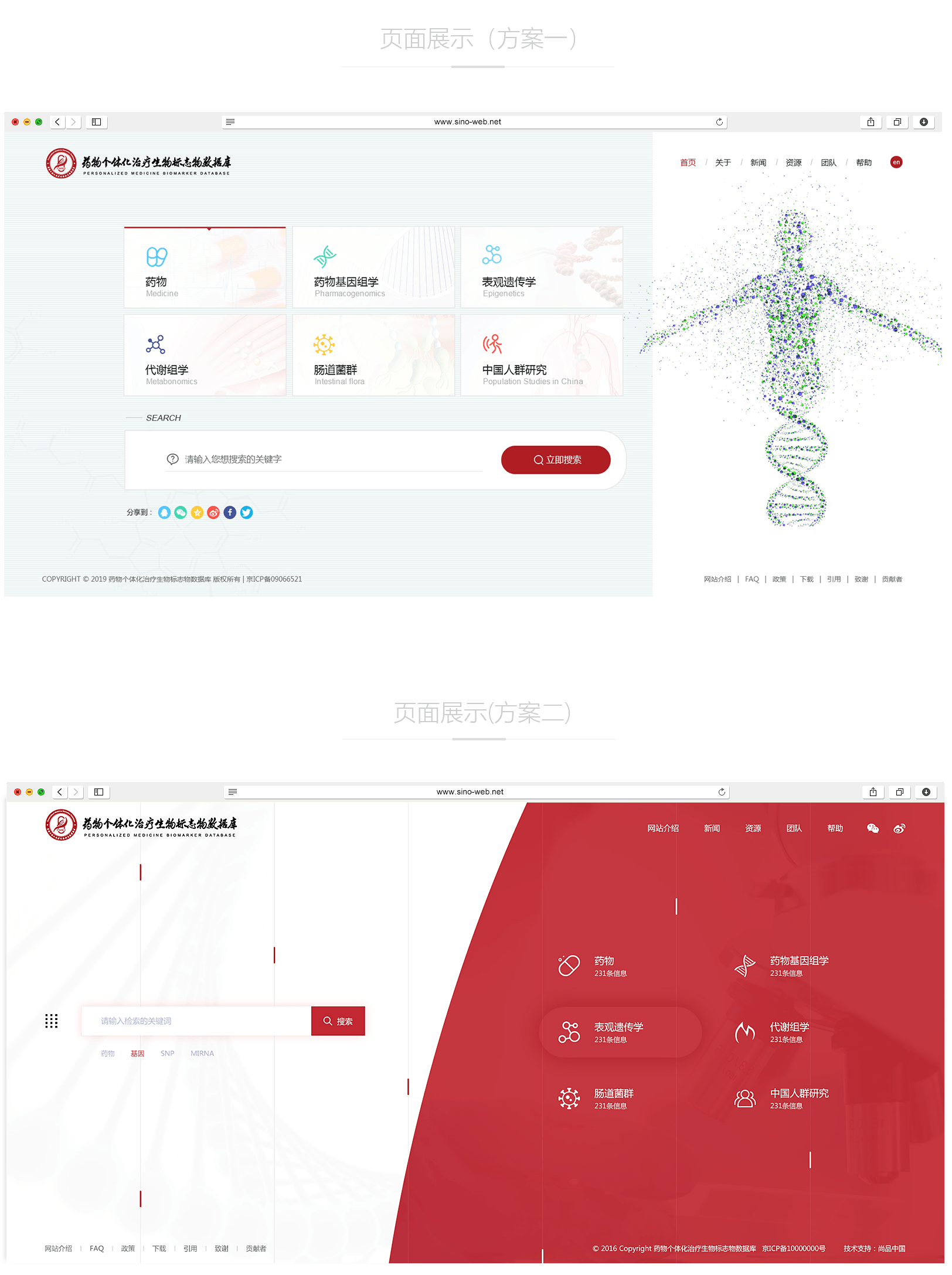
-
-
Data encryption and transmission security: Encrypt the sensitive data in the website cluster to ensure the security of data in transmission and storage. -
Use HTTPS protocol to ensure encryption during data transmission. -
Encrypt and store the sensitive data in the database.
-
-
Security vulnerability scanning and repair: Regularly scan the security vulnerabilities of the website cluster, and timely repair the possible vulnerabilities. -
Use automated vulnerability scanning tools while conducting manual code reviews. -
Timely repair and upgrade the vulnerabilities found.
-
-
Emergency response plan: Make plans to deal with emergency security incidents, including network attacks, data leakage, etc. -
Prepare an emergency contact list to ensure that actions can be taken quickly in case of security incidents. -
Implement emergency safety response measures to limit risks and damages.
-
-
Data backup and recovery: The website cluster data shall be backed up regularly to ensure timely recovery in case of data loss or damage. -
Use offline and remote backup to ensure the integrity of backup data. -
Regularly test the data recovery process to ensure that the backup strategy is effective.
-
-
Cooperation between suppliers and third parties: If external suppliers, partners or cloud service providers are involved, ensure that they also comply with security standards. -
The signing of the contract requires the partners to comply with the safety policy and regularly review their safety measures.
-
-
Continuous monitoring and logging: Set up a monitoring system for security incidents and record logs to track and investigate potential security problems. -
The security information and event management (SIEM) system is used to monitor abnormal activities and record event logs.
-
-
Staff training and awareness raising: Train employees to identify social engineering and phishing attacks and enhance security awareness. -
Regularly organize security training and share the latest network security threats and prevention methods.
-
-
Technical updates and upgrades: According to the technical development and demand changes, regularly assess whether the system technology needs to be updated and upgraded. -
Update the operating system, application programs and related software, and repair the vulnerabilities in a timely manner.
-
Station building process
-
Website requirements -
Website planning scheme -
Page design style -
Confirm delivery for use -
Data entry optimization -
Program design and development -
Follow up service -
contact number 010-60259772
Hot tags
-
Shanghai website construction -
WeChat applet development -
Applet development -
Liuzhou website construction -
Fuzhou website construction -
Baoding website construction -
Qingdao website construction -
Jilin website construction -
Cangzhou website construction -
Shenzhen website construction -
Shanghai Website Design -
Xi'an website construction -
Chengde website construction -
Shenyang website construction -
Langfang website construction -
Zhengzhou website construction -
Jinan website construction -
Shijiazhuang website production -
Tianjin website construction -
Beijing website construction
Latest articles
-

Website construction scheme: Fresh makeup aesthetics website Type: website construction 2025-03-13 -

Enterprise website construction plan: create a new business card for the network and open the digital future Type: website construction 2025-03-11 -

High end website production solution Type: website construction 2025-02-18
Recommended News
-
What are the requirements of Beijing state-owned enterprise website construction? Legal compliance: comply with relevant laws and regulations, including the Regulations of the People's Republic of China on Telecommunications and Internet Management 2024-07-17 -
Is Beijing website construction company reliable? How about the design? When designing websites, many people want to cooperate directly with professional website construction companies, so that they can ensure that 2023-09-02 -
How does Tianjin website construction present rich content? See what you can do After the website is successfully built, the company must fill in various contents in the website. Tianjin website construction company suggests that everyone 2021-04-20 -
Six Elements of Shanghai Enterprise Website Design Can't be Ignored While pursuing a good looking website, we should also consider the overall layout of the website. When we do a website 2021-08-14 -
What details should be paid attention to when building Zhengzhou website? With the development of the Internet, more and more enterprises choose to expand their business on the Internet. If they want to be with each other 2021-09-21 -
What are the aspects of high-quality service of Xi'an website construction? At present, there are more and more professional platforms for building websites in China, and their website building business is basically all over the country 2021-07-14
Make an appointment with a professional consultant to communicate!
Disclaimer



