-
simplified Chinese character -
Simplified Chinese English
Shangpin China Joins Hands with Beisheng Internet to Create a New Chapter in Website Construction
Network security: flow chart of web firewall
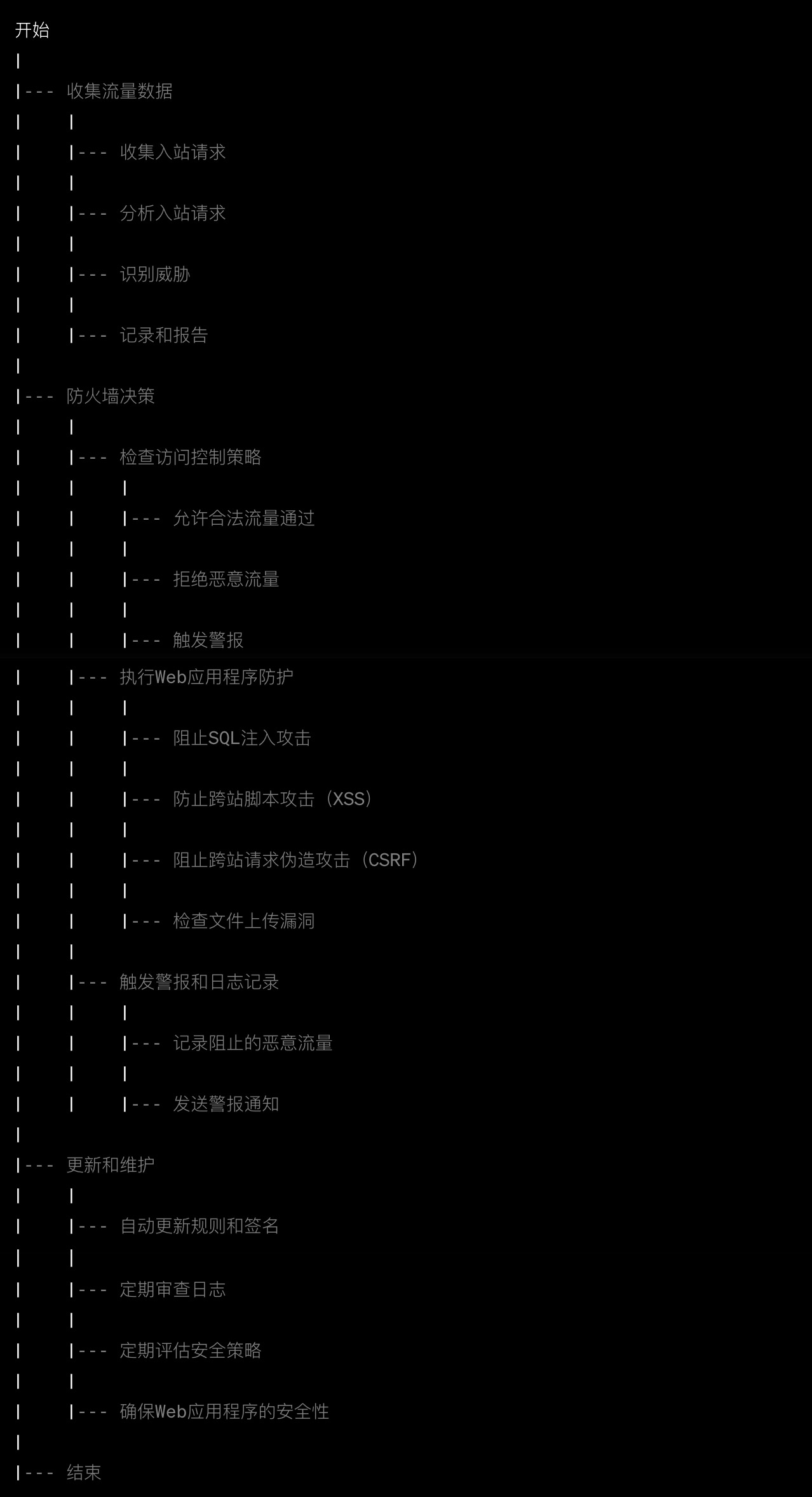
Station building process
-
Website requirements -
Website planning scheme -
Page design style -
Confirm delivery for use -
Data entry optimization -
Program design and development -
Follow up service -
contact number 010-60259772
Hot tags
-
WeChat applet development -
Applet development -
Luoyang website construction -
Beijing website customization development -
Shenyang Website Design -
Zhengzhou website design -
Langfang Website Design -
High end website design -
Website Design -
Shijiazhuang website production -
Tianjin website construction -
Education website construction -
Website production
Latest articles
-

Website construction scheme: Fresh makeup aesthetics website Type: website construction 2025-03-13 -

Enterprise website construction plan: create a new business card for the network and open the digital future Type: website construction 2025-03-11 -

High end website production solution Type: website construction 2025-02-18
Recommended News
-
What are the advantages of flat website design? Now people prefer simple and direct things, and the most direct response is in website design. With 2021-06-01 -
What are the specific requirements for high-end website design? In order to better highlight the style and characteristics of high-end websites and improve the publicity effect of the entire website, the most important thing is 2021-04-06 -
How much will game website design cost in 2022? As the market demand for website construction is growing, many small and medium-sized enterprises have to do website construction, so that the city 2023-04-14 -
What are the good plans for building mother and baby websites? Take a look The mother and baby industry is a huge market, and it is also the industry most suitable for entering e-commerce. The website of mother and baby industry 2021-03-11 -
What are the characteristics of enterprise customized websites With the rapid development of the Internet, corporate websites are also facing upgrading. The previously built website and template website are not suitable 2021-10-19 -
How to develop platform websites? First of all, platform websites need to identify their target users, and tailor services to target users 2024-05-30
Make an appointment with a professional consultant to communicate!
Disclaimer



