1. Network load balancing. For service ears (such as 1eb. FTP transaction name, etc.) that are required to respond to access requests from large users at the same time, it is difficult to meet users' performance requirements by using only a single server. Network load balancing can be used. Multiple servers running the same application or mask can be clustered together and a virtual B 'address can be shared. Clients can access servers in the cluster through the virtual IP address, The network load balancing task distributes the user's access to different servers in the cluster. When a mask fails, the network load balancing task will be redistributed among other servers, thus providing high performance and high availability for application leases The NLB (Network Load Balancing) function of Windows Server 2003 can cluster up to 32 servers together
2. Server cluster allows clients to still access applications and resources in the event of failure or planned downtime. For example, a player in Lai cluster cannot be used due to failure or male protection, The resources and application leases will be transferred to the available cluster nodes. For the "Windows Cluster. Solution", use the "High availability. This term is more appropriate than fault tolerance. Server clusters cannot guarantee uninterrupted operation, but they can indeed provide sufficient availability for most key task applications. Cluster services can monitor applications and resources, and can automatically identify and recover numerous failure conditions, which provides flexibility for managing work in clusters. In addition, the availability of the whole system is improved
From the above comparison, it can be seen that network load balancing emphasizes redundancy and load balancing, which is suitable for situations that only provide browsing or subordinate services. Server clusters emphasize high availability, which is more suitable for situations that require users to submit data. This experiment only introduces network load balancing.
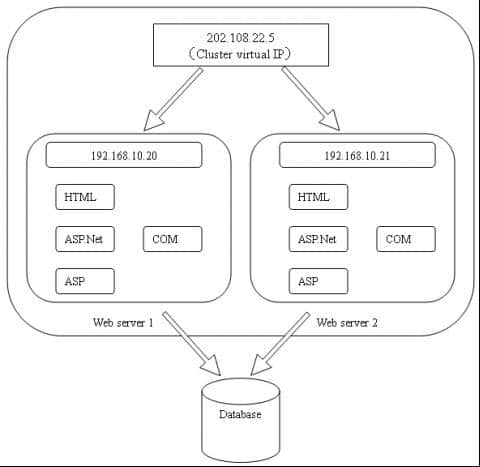
Network load balancing uses a cluster composed of two or more hosts working together to provide high availability and scalability of Web servers or other application servers, and clients use a single IP address to access the cluster. The client cannot distinguish between a single server and a cluster. The server program cannot identify whether they are running in a cluster. However, a cluster with network load balancing is obviously different from a single host running a single server program. This is because even if a cluster host fails, a cluster with average network load can provide uninterrupted services. The cluster can also respond to customer requests faster than a single host. If a host fails or goes offline, network load balancing provides high availability by targeting the received network traffic to the working cluster host. When the existing connection with an offline host is lost, in most cases (for example, when using a Web server), the client software will fl automatically retry the failed connection, and there is only a few seconds delay when receiving the response.
Network load balancing achieves performance scalability by distributing incoming network traffic to one or more virtual IP addresses assigned to the network load balancing cluster. Hosts in the cluster can respond to different customer requests at the same time, even if multiple requests from the same host. For example The Web browser can display multiple images from different hosts in the network load balancing cluster in one Web page, which can speed up the processing of customer requests and shorten the response time to customers. In a single subnet, all hosts using the network load balancing cluster simultaneously check the network communication received on the primary IP address of the cluster (and other IP addresses of multi host hosts). On each cluster host, the network negative balance driver acts as a filter between the cluster adapter driver and TCP/IP, allowing the host to receive some incoming network traffic.
Network load balancing uses a complete distributed algorithm to make statistics and map the IP address, port and other information of the foreign client to the cluster host. When checking the arrived packet, all hosts execute the mapping at the same time to quickly determine the host responsible for processing the packet. This mapping remains unchanged unless the number of cluster hosts changes. In order to coordinate these operations, the network load balancing host periodically exchanges multicast or broadcast messages within the cluster. This allows them to monitor the status of the cluster. When the cluster state changes (such as the host fails, leaves or joins the cluster), network load balancing calls a process called dispersion. In this process, the host exchanges messages to determine the new consistent state of the cluster, and selects the host with the highest host priority as the master. When all cluster hosts agree on the new state of the cluster, they will record the completion of convergence in the Windows Server 2003 event log.
During the convergence process, the normal host continues to process the received network communication, but the faulty host cannot receive the customer request, and the working host customer request is not affected. At the completion of convergence, the communication of the failed host is redistributed to the remaining hosts. If a host is added to the cluster, it is allowed to take over the processing of the port and receive the load balance communication it undertakes. Cluster expansion does not affect ongoing cluster operations and is transparent to client and server side programs. However, since the client side may be remapped to different cluster hosts, it may affect client sessions that span multiple TCP connections.
Network load balancing assumes that the host in the cluster is normal as long as it can exchange messages with other hosts in the cluster. If other hosts cannot receive a response from a member during certain periods of message exchange, they will initiate convergence to redistribute the load handled by the failed host. The user can control the message exchange cycle and the number of lost messages required to start convergence. The default value is 1000 milliseconds (Is) and 5 lost messages respectively. Since these parameters are not often modified, they cannot be configured with "w" in the "Network Load Properties" dialog box. If necessary, they can be adjusted manually in the registry.