-
simplified Chinese character -
Simplified Chinese English
Shangpin China Joins Hands with Beisheng Internet to Create a New Chapter in Website Construction
Internet Network Architecture
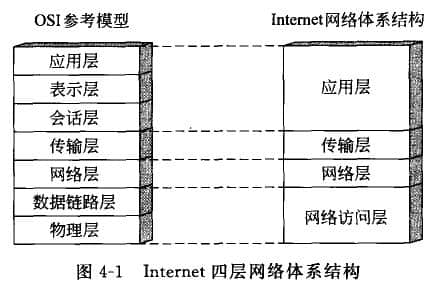
-
HyperText Transfer Protocol -
File Transfer Protocol -
Simple Mail Transfer Protocol -
Post Office Protocol 3 -
Telnet -
Simple Network Management Protocol
-
Connection oriented and reliable transmission control protocol TCP (Transmission Control Protocol) -
UDP (User Datagram Protocol) for connectionless and unreliable user datagram protocol
-
Internet Protocol (IP) that provides connectionless and unreliable services -
Internet Control Message Protocol (ICMP) of the secondary IP protocol, -
Address Resolution Protocol -
Internet Group Management Protocol (IGMP) -
Reverse Address Resolution Protocol (RARP)
Station building process
-
Website requirements -
Website planning scheme -
Page design style -
Confirm delivery for use -
Data entry optimization -
Program design and development -
Follow up service -
contact number 010-60259772
Hot tags
-
Website construction -
Food website construction -
WeChat applet development -
Applet development -
Wuxi website construction -
Website construction of research institute -
Shenyang website construction -
Langfang website construction -
Zhengzhou website construction -
Construction of wedding photography website -
Mobile terminal website construction -
University website production -
Tianjin website construction -
Education website construction -
Brand website construction -
Government website construction -
Beijing website construction -
Website Design -
Website production
Latest articles
-

Website construction scheme: Fresh makeup aesthetics website Type: website construction 2025-03-13 -

Enterprise website construction plan: create a new business card for the network and open the digital future Type: website construction 2025-03-11 -

High end website production solution Type: website construction 2025-02-18
Recommended News
-
Organization and design of website appearance When designing and creating a Web site, the organizational structure is important, but don't ignore the appearance 2015-08-07 -
Some suggestions to avoid in website construction In today's society, the website has become one of the indispensable marketing methods for an enterprise 2020-10-21 -
Six preparations should be made in the early stage of website construction With the advent of the Internet era, more and more people attach importance to the traffic brought by the Internet. A large number of business owners 2021-06-18 -
How to make perfect seo website optimization scheme When the webmaster gets the website optimization, he doesn't get a website to do the keyword outside the chain. The first step should be to 2013-07-22 -
Shangpin China Background Video Tutorial (4) Content Editor This video mainly introduces the tips of using the content editor, how to copy and paste the content editor in a word document 2015-07-27 -
Analysis of the reasons for Baidu dropping its power on the website If you follow Baidu's algorithm to improve the website ranking, remind the majority of SEO optimization personnel. Take 2013-06-27
Make an appointment with a professional consultant to communicate!
Disclaimer



