Transmission of IP datagrams
Source: Shangpin China |
Type: website encyclopedia |
Time: June 26, 2014
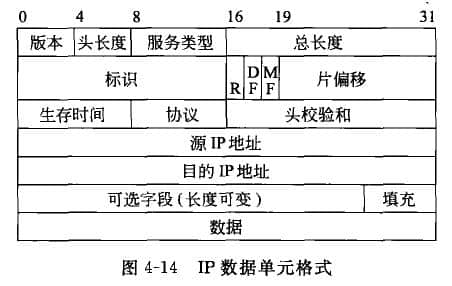
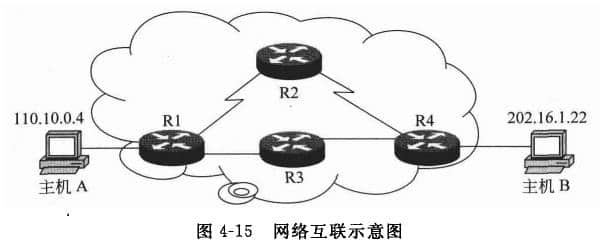
The emergence of network layer is also the result of network development. When the data communication needs to cross the network segment and there are multiple communication paths to choose, the problem of how to connect any two hosts for long-distance data transmission arises. The IP protocol of the network layer solves this problem well. Here we need to understand the IP protocol and the format of the IP data unit, and then analyze the working principle of the IP protocol. 1. IP protocol IP protocol (Internet Protocol) is the interconnection protocol between networks. IP protocol is a set of agreements or rules that all computers connected to the Internet can communicate with each other. This set of rules ensures that functions such as inter network connection, inter network addressing and inter network data forwarding can be realized. Therefore, it is the most important protocol in the network layer. Together with TCP protocol, it forms the core of TCP/IP protocol family IP protocol provides connectionless and unreliable data transmission services in the network layer. What is connectionless and unreliable data transmission? The transmission of IP packets on the network layer is like ordinary mail sent in the post office in our life. Each ordinary mail has a definite destination address. The ordinary mail may take different paths in the transmission process. There is no guarantee for ordinary mail on the way of sending; There is no direct restriction relationship between the sender and the receiver, a pair of related subjects (which can be understood as disconnected). If ordinary mail is lost during transmission, the post office is not responsible (which can be understood as unreliable). That is to say, in the network transmission of IP packets, there is no need to establish a network layer between the sending end and the receiving end Beijing Website Design For connection, the network layer of the sender does not need to care whether the IP packet is sent to the network layer of the receiver. 2. IP data unit format The data unit of IP protocol is also very complex, as shown in Figure 4-14. The IP protocol header is mainly composed of 12 domains, and the data units transmitted from the transport layer constitute the IP datagram of the network layer, also known as IP packet. The composition of the IP protocol header is 32 bits per row, and the meaning of each domain is explained as follows. Version: refers to the IP protocol version number, currently 4, that is, the Internet Header Length (IH L): refers to the length of the IF protocol header, which takes 4 Bs as a unit, and the minimum value is 5, that is, the smallest IP protocol header has 20 bytes (when there is no option). Type of Service (TOS): It consists of 8 bits. Bit settings at different locations can represent different service types. There are service types such as data priority (now ignored), low latency, high throughput, high reliability, and minimum cost. Otherwise, it means a general service. Total Length (TL): refers to the length of the entire IF package, in B. Using the length of the protocol header and the total length, you can know the starting position and length of the data in the IF packet. Identification: identifies the ID of each IF packet sent by the host, accounting for 16 bits. Usually, its value will be increased by 1 for each IP packet sent. The IF packet is a data unit transmitted at the network layer, and different network types have the feature of MTU limitation at the link layer. For example, the MTU of Ethernet is 1500B, which is the maximum value of the IP protocol data unit at the network layer. If the total length of the IP packet exceeds the MTU, the network layer will partition the IF packet so that the length of each packet is less than or equal to the MTU. At this time, the 16 bit ID will be copied to each message after the IF packet is partitioned. At the receiving end, the reorganization basis of the datagram slice is this ID. R: Leave unused. DF (Don't Fragment): IP packets are not partitioned, accounting for 1 bit. A value of 1 indicates that the network layer will not partition IP packets. MF (More Fragment): the flag of a piece. A value of 0 indicates that the current datagram is the last piece; A value of 1 indicates that it is not the last report, and there are other reports later. Fragment Offset (FO): the position where the piece is offset from the beginning of the original datagram. The number of bytes offset is the offset value multiplied by 8. In addition, when the IP packet is partitioned, the total length of each piece should be changed to the length of the piece. The receiver receives the last piece of message, calculates the total length of the datagram from its length and piece offset, compares it with the length of all the arrived pieces, judges the integrity of the piece of message, and then reconstructs it. Time To Live (TTL): sets the maximum number of routers that IP packets can pass through (refer to the explanation of questions 4-5 in Chapter 11 for the unit of TTL). The initial value of TTL is set by the source host. After passing through a router, its value decreases by 1. When the value of this field is 0, the IP packet is discarded by the router and sent an ICMP message to notify the source host. Protocol (PROT): indicates the protocol type of the upper layer. Specifically, it refers to the protocol coding of TCP or UDP. Header checksum: It is the "checksum" code calculated according to the IP protocol header. If the "checksum" is incorrect, the IP packet will be discarded, but no error message will be generated. The retransmission control will be controlled by the transport layer to discover discarded datagrams and retransmit them. Source IP address: Each IP packet must contain the source IP address of the sender, which is a 32bit value. Destination IP address: Each IP packet also needs to contain the IP address of the receiving end, which is also a 32bit value. Optional field (Options): a variable length option, used for security, debugging, etc., and also for future expansion or upgrading (see Chapter 11, Question 4-6, for the application of this field). Padding: insert a certain number of padding bytes when necessary to ensure that the IP protocol header is always an integer multiple of 32bit. Data: the protocol data unit submitted by the transport layer. From the protocol header of the IP packet, there are two sizes of the IP protocol header: when there is no "option" field, it is 160 bits or 20 bytes; When there is an "option" field, it is 192 bits, that is, 24 bytes. 3. Operating principle of IP protocol How does IP realize network interconnection? In the early days, the network systems of various companies could not be interconnected. The reason is that the format of the basic data unit (data frame) they transmit in their respective networks is different. With IP protocol, different network systems are interconnected. It can be understood that lip protocol is a set of protocol software composed of programs. It converts various "data frames" into "IP packet" format to realize transmission on the Internet. This conversion is one of the most important characteristics of the Internet. It enables heterogeneous network computer systems to communicate with each other on the Internet, and also makes the Internet have the true meaning of "openness". So, what is an "IP packet"? From the composition of the IP data unit format, it can be seen that the IP packet is a connectionless and independent data transmission unit, which carries clear identifications (i.e. IP address) such as where the data comes from and where it will be sent. In this way, when IP packets are transmitted between networks, it is not necessary to establish a data channel first, but each IP packet can be independently transmitted to the destination via different transmission paths. [Example] As shown in Figure 4-15, the basic working principle of IP protocol is analyzed. When the two communication ends (host A and host B) are located in different networks, data transmission needs to be transmitted across the network through the router. The sending end A only needs to deliver the IP packet (to be partitioned first if needed) to the first router RI. Router R1 selects the path and forwards it to the next router (R2 or R3) according to the destination ID carried by the IP packet. The next router forwards it to its next router R4, which finally transmits the IP packet to the destination host. At the B end of the destination host, after receiving the IP packet, the protocol header checksum will be checked, and the failed IP packet will be discarded directly (no error message will be sent back to the sender); The IP packet extracted datagram data without error is directly delivered to the upper transport layer. It can be seen that the transmission of IP packets at the network layer is not only connectionless, but also the arrival of IP packets at the destination end is unordered and unreliable. 4. Other network layer protocols In the network layer, in addition to the very important IP protocol, there are two more important protocols that are briefly introduced below. 1) ICMP protocol ICMP (Internet Control Message Protocol) is a sub protocol of TCP/IP protocol family, which is mainly used to transfer control information between hosts and routers. These control messages refer to the messages of the network itself, such as whether the network is unblocked, whether the host is reachable, whether the route is available, and whether the IP packet routing has exceeded the "lifetime". They also include control and status information such as error reporting and exchange restriction. Although these control messages do not transmit user data, they play an important role in the transmission of user data. In network applications, we often get messages provided by ICMP, but they are often ignored. If a host is in a shutdown or maintenance state and does not provide network services, ICMP can give a Destination Unreachable notification to the initiated TCP connection, informing the host that it is unreachable. For another example, when checking whether the network is unblocked, we often use the ping command. This command is an application based on the ICMP protocol. The information returned by the ping command is a report provided by the ICMP protocol. 2) ARP protocol ARP (Address Resolution Protocol) is used to resolve the physical address (48 bit MAC address) of the host through its network address (32-bit IP address). In the Internet, under the network layer is the network access layer, which corresponds to the data link layer and the physical layer of the LAN. In the data link layer, data communication takes "data frame" as the transmission unit, and the addressing mode of "data frame" is realized according to the MAC address of the communication ends. Therefore, after the IP packet of the network layer enters the network access layer, the next transmission must know the physical address of the next link point or destination node, that is, the MAC address. How to find the MAC address of the next link point or destination node is implemented by the ARP protocol.
Source Statement: This article is original or edited by Shangpin China's editors. If it needs to be reproduced, please indicate that it is from Shangpin China. The above contents (including pictures and words) are from the Internet. If there is any infringement, please contact us in time (010-60259772).