Transmission of TCP/UDP datagrams
Source: Shangpin China |
Type: website encyclopedia |
Time: June 26, 2014
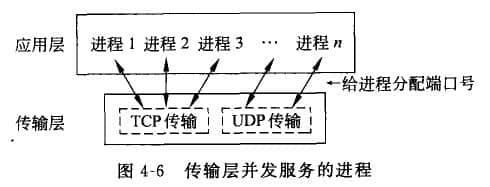
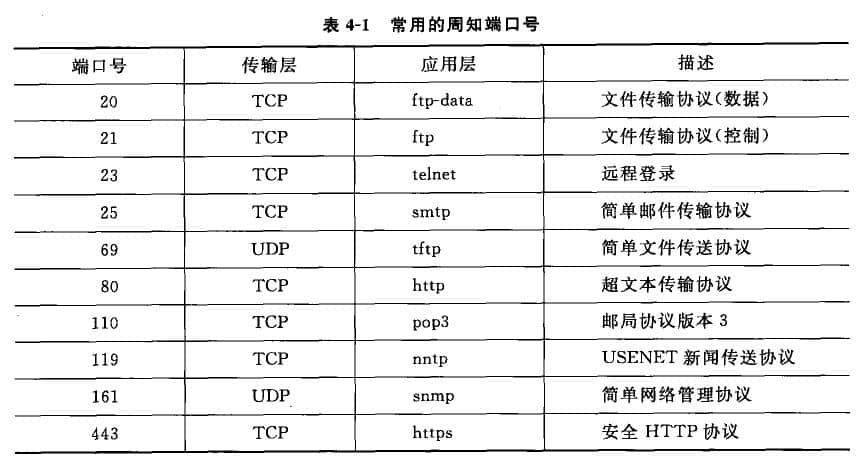
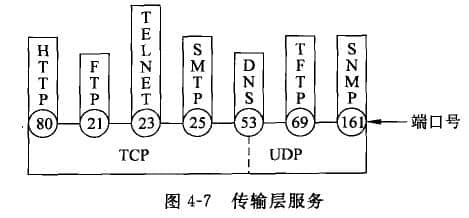
Two data transmission services are provided in the TCP/IP transport layer, namely TCP and UDP. On the Internet Beijing website construction In the network architecture, the transport layer plays an important role, and it needs to be analyzed from the data unit format of these two transport services. First, there is a very important concept reference in the transport layer, that is, port. 1. Port The port is used to distinguish between different application processes or different connections. In practical applications, multiple IE browsing windows are often opened at the same time to browse the Web resources of different sites, or there are other network application windows. In a computer system, every application opened means that at least one process is opened (refer to question 4-1 in Chapter 11 for the definition of process). Multiple IE windows open multiple processes. Then, when datagrams generated by each process of the application layer pass through the transport layer services, the problem that TCP or UDP provides concurrent services for multiple application processes at the same time will be encountered, that is, multiple application processes may need to transmit data through the same TCP or UDP protocol service access point, as shown in Figure 4-6. In order to distinguish different application processes or connections in the upper layer, when the application layer protocol interacts with the transport layer protocol, the transport layer uses different port numbers to describe the communication paths of the upper layer applications in the transport layer. Therefore, the port number is a very important identification mark for the upper application process. Port numbers are divided into two categories: well-known ports and dynamic ports. 1) Well known port Well Known Ports: From. To 1023. These ports are tightly bound to some services and indicate the application layer protocol of this service. This type of port adopts global allocation, which is a centralized control mode. A recognized central agency will uniformly distribute according to user service needs, and publish the results to the public. For example, port 80 clearly tells all customers that the application layer is HTTP protocol communication and port 21 is FTP protocol communication. If there is a server that provides Web services and hopes that users all over the world can access its resources, it must open port 80 and wait on the port to provide HTTP services for customers at any time 2) Dynamic Port Dynamic Ports: from 1024 to 65535. The reason why they are called dynamic ports is that they are not always assigned to a specific application. This type of port adopts local allocation, which is a dynamic control mode. If a process needs transport layer services, it first needs to apply for a port to the local operating system. The operating system returns a local unused port number randomly from the available dynamic port numbers. The process then binds the process with the port number obtained through the system call. When the process is closed, the occupied port number is also released. [Example] If the client opens the Yahoo Messenger application, then at least two session processes should be opened on the client. Two dynamic ports randomly obtained should be used to establish connections with the Yahoo server and the account verification center respectively. For example, a process connection is the local port 2192 and Yahoo. The other process is the connection between the local port 2196 and the Yahoo account authentication center port 433. 2192 and 2196 are the port numbers dynamically assigned by the client, 433 is the service port of the Yahoo account verification center, and 5050 is the service port of the Yahoo server (here, the service port 5050 is specified from the dynamic port number, which can be found in many practical applications, such as QQ applications). When a customer chats with an online friend via the Yahoo Messenger chat window, a new conversation process will be established on the client, such as the connection between the local port 5101 and the opposite port 4548. If you want to leave a message for an offline friend, the message information will be transferred to the Yahoo server locally through the established connection between the local port 2192 and the Yahoo server port 5050, and then the Yahoo server agent will transfer the message information to the other party. See Table 4-1 for commonly known port numbers. 2. TCP/UDP protocol 1) TCP protocol TCP (Transmission Control Protocol) is a connection oriented and reliable transmission communication protocol. What is connection oriented? To transmit data between peer transport layers, the sender and receiver must first establish a logical communication link for data transmission (TCP's "triple handshake" is explained later). After data transmission, the connection must be disconnected. The reason for reliable transmission is that TCP can ensure the integrity of data transmission between the sending end and the receiving end (no loss, no misinformation), that is, the receiving end must send back the confirmation information to the sending end after each TCP datagram received from the corresponding layer of the sending end is verified to be correct, otherwise the sending end will retransmit. This data transmission method is just like the telephone communication in our daily life. First, we need to establish a call connection, then start a call, and finally disconnect the connection. Therefore, the data transmission of this service mode is suitable for the application where a large number of data are transmitted at one time and reliable transmission is required. 2) UDP protocol UDP (User Datagram Protocol) is a simple communication protocol for connectionless and unreliable transmission. UDP connectionless communication, that is, the sender UDP receives the datagram transmitted from the upper application, adds the UDP protocol header information, and then directly delivers it down to the network layer. Its unreliable transmission means that after receiving the UDP datagram, the receiving end directly submits the datagram data that has no problem in verification to the upper layer, and does not need to send back confirmation to the sending end; The datagram with problems in verification is lost directly. Because the lost datagram does not need to be retransmitted, the integrity of the transmitted data cannot be guaranteed. This data transmission mode is just like the ordinary mail sent through the post office in our daily life. The sender can just drop the letter into a mailbox, regardless of whether the letter can be delivered; The recipient is not enough to confirm with the sender after receiving the letter. This service mode of data transmission is suitable for applications with small amount of transmission at one time and low reliability requirements. As shown in Figure 4-7, the application layer requires the transport layer to provide reliable transport services such as HTTP, FTP, Telnet and SMTP, all of which require high reliability and integrity. The data transmitted by TFTP and SNMP at both ends are very simple data, such as network device configuration information or network management information. Basic data transmission requirements can be met through UDP. There are also instant messaging tools such as QQ. In the case of good network communication, voice data is transmitted preferentially using UDP. Because the use of UDP can reduce the additional cost of the channel, it does not need to establish and maintain the connection, and it does not need to transfer the confirmation message from end to end; The UDP protocol header itself is much smaller than TCP, which also reduces the bandwidth occupied by the channel and improves the data transmission rate of the channel.
Source Statement: This article is original or edited by Shangpin China's editors. If it needs to be reproduced, please indicate that it is from Shangpin China. The above contents (including pictures and words) are from the Internet. If there is any infringement, please contact us in time (010-60259772).