-
simplified Chinese character -
Simplified Chinese English
Shangpin China Joins Hands with Beisheng Internet to Create a New Chapter in Website Construction
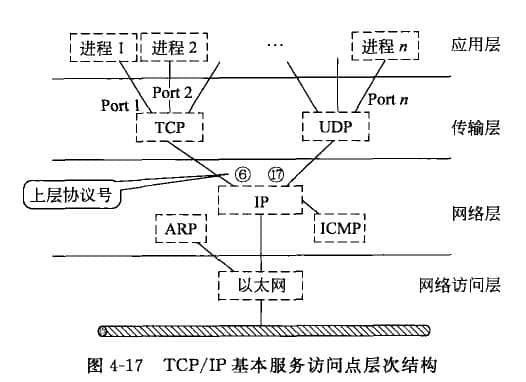
TCP/IP layer protocol communication flow
Station building process
-
Website requirements -
Website planning scheme -
Page design style -
Confirm delivery for use -
Data entry optimization -
Program design and development -
Follow up service -
contact number 010-60259772
Hot tags
-
Website construction -
Food website construction -
WeChat applet development -
Applet development -
Wuxi website construction -
Website construction of research institute -
Shenyang website construction -
Langfang website construction -
Zhengzhou website construction -
Construction of wedding photography website -
Mobile terminal website construction -
University website production -
Tianjin website construction -
Education website construction -
Brand website construction -
Government website construction -
Beijing website construction -
Website Design -
Website production
Latest articles
-

Website construction scheme: Fresh makeup aesthetics website Type: website construction 2025-03-13 -

Enterprise website construction plan: create a new business card for the network and open the digital future Type: website construction 2025-03-11 -

High end website production solution Type: website construction 2025-02-18
Recommended News
-
Shijiazhuang website construction tells you why website domain names are particularly important for enterprises The importance of having your own domain name need not be emphasized. If there is no domain name business on the Internet, it will lose a lot 2022-07-07 -
How to find users' needs in website construction? In reality, there are many failure cases of websites. For example, some websites blindly pursue cool page design, and even 2019-09-04 -
Characteristics of Network Teaching Information Resources The Internet has turned unrealistic things into reality, such as website design, online teaching, online teaching and dissemination 2015-08-20 -
Tianjin website construction teaches you how to build an excellent enterprise website? Look at these methods Although the Internet has developed for many years, there are still many entities that do not attach importance to the construction of enterprise websites. Here 2022-06-29 -
What are the misunderstandings of online marketing Network marketing is a hot topic nowadays, and it is the hot spot in the hearts of many promotion personnel. Once it is done well, the brand building network 2015-02-24 -
What are the styles of customized website design? How about each style? Most people pay more attention to the style of customized website design. In many cases, we may have more 2023-09-28
Make an appointment with a professional consultant to communicate!
Disclaimer



