Working mode and main functions of DBMS
Source: Shangpin China |
Type: website encyclopedia |
Time: June 16, 2014
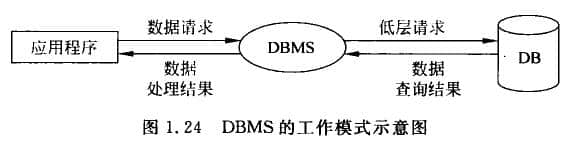
The database management system manages data Website production Software system is the core component of database system. All operations of users in the database system, including data definition, query, update and various controls, are carried out through DBMS. The working diagram of DBMS is shown in Figure 1.24. The working mode of DBMS is as follows:
(1) Accept data requests and processing requests from applications; (2) Convert user's data request (high-level instruction) into complex machine code (low-level instruction); (3) Realize the operation of database; (4) Accept query results from database operations; (5) Processing query results; (6) Return the processing results to the user.
DBMS is always based on a certain data model, so DBMS can be regarded as the specific implementation of a certain data model on a computer system. According to different data models, DBMS can be divided into hierarchical, network, relational, object-oriented, etc.
In different computer systems, due to the lack of unified standards, even DBMSs with the same data model are often different in terms of user interfaces, system functions, etc.
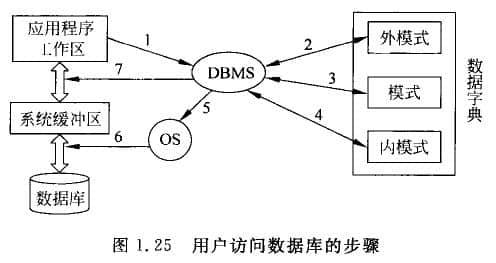
In order to give the reader an overall concept of database system work, this paper takes query as an example to introduce the main steps of accessing the database, as shown in Figure 1.25.
(1) When executing a record in the application program to query the database, issue a command to the DBMS to read the corresponding record and indicate the external mode name.
(2) After receiving the command, the DBMS calls out the required external mode and checks the permissions. If it is legal, continue to execute; Otherwise, an error message is returned to the application.
(3) DBMS accesses the mode and determines the information about the required data in the mode (logical record type) according to the external mode/mode image.
(4) DBMS accesses the internal mode and determines the relevant information (read physical record and access method) of the required data on the internal mode according to the mode/internal mode image.
(5) The DBMS sends a request to the operating system to read the corresponding data (read records).
(6) The operating system executes the read command to transfer the relevant data from the external memory to the system buffer.
(7) DBMS sends the data to the user's work area in the form of external mode, and returns the information of normal execution, so that the user program can use the data. Of course, these are just a few big steps, not related details. It can be seen from the above that DBMS is the core of the database system and is related to the operating system.
The main functions of DBMS are as follows:
1. Database definition function
DBMS provides a data definition language (DDL), which defines the three-tier schema structure of data, including schema, outer schema and inner schema, defines the secondary image of schema/inner schema and outer schema/schema, and defines relevant constraints. For example, user passwords and access permissions defined to ensure database security, and integrity rules defined to ensure correct semantics.
2. Data manipulation function
DBMS provides the data manipulation language DML to realize the basic operations of data in the database, such as retrieval, insertion, modification, deletion and sorting. There are two types of DML:
(1) Embedded DML. It includes DML embedded into high-level languages such as C++or PowerBuilder (called host language).
(2) Non embedded DML. It includes interactive command language and structured language. Its syntax is simple and can be used independently. It is executed by a separate interpretation or compilation system, so it is generally called autonomous or self-contained DML. The command language is a line structure language, which is executed individually; Structured language is the extension and development of command language, which adds program structure description or process control functions, such as loop, branch and other functions. Command languages are generally interpreted and executed item by item. Structured languages can be interpreted and executed, and can also be compiled and executed. Now DBMS generally supports interactive environment of command language and structured language environment for users to choose.
3. Database protection function
The data in the database is the strategic resource of the information society, and the protection of data is a crucial event. DBMS protects the database through four aspects, so DBMS includes the following four subsystems:
(1) Database recovery. When the database is damaged or the data is incorrect, the system has the ability to restore the database to the correct state.
(2) Concurrency control of database. When multiple users operate the same data at the same time, the system shall be able to control it to prevent data in the database from being damaged.
(3) Data integrity control. Ensure the correctness and validity of the data and semantics in the database, and prevent any operation that causes errors to the data.
(4) Data security control. Prevent unauthorized users from accessing data in the database to avoid data leakage, change or destruction.
Other protection functions of DBMS include system buffer management and some adaptive adjustment mechanisms for data storage.
4. Database maintenance function
It includes the functions of installing the initial data of the database, dumping, restoring, reorganizing the database, and monitoring and analyzing the system performance. These functions are completed by various utilities.
5. Data dictionary
The database in which the three-layer structure definition is stored in the database system is called data dictionary (DD). The database operation can only be realized through DD What information should be included in DD is not clearly defined, which is generally determined by the function of DBMS. There are two main types of data: one is information from users, such as the definition of tables, views (virtual tables used by users), indexes, and user permissions; The other is statistical information from system status and database, such as protocol used by communication system, mapping relationship between database and disk, frequency statistics of data usage, etc. The above are the functions of general DBMS. DBMS functions that are usually implemented on large and medium-sized computers are strong and complete, while DBMS functions that are implemented on microcomputers are weak.
Source Statement: This article is original or edited by Shangpin China's editors. If it needs to be reproduced, please indicate that it is from Shangpin China. The above contents (including pictures and words) are from the Internet. If there is any infringement, please contact us in time (010-60259772).