Hacker and Network Security
Source: Shangpin China |
Type: website encyclopedia |
Time: 2015-06-17
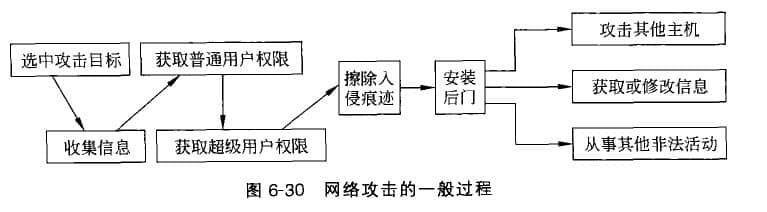
China Internet Network Information Center found that in the first half of 2010 alone, 59 2% of netizens have encountered virus or trojan attack in the process of using the Internet, and 30.9% of netizens' accounts or passwords have been helmeted. The Internet should move from online entertainment to the deep application and development of online commerce, and network security has become the primary constraint. 1. Hackers and network attack targets Hacker is a transliteration of Hacker, which originally refers to the specialized research and discovery of computers and Website construction The computer enthusiasts of loopholes have played an active role in the development and improvement of computers and networks. Now, the term "hacker" has been used to refer to those who use computers to do damage or mischief. In fact, the correct English name for these people is Cracker. Some people translate it as "hacker". Network attack or human intrusion refers to the act of illegally entering other people's systems (hosts or networks) without authorization by taking advantage of system security vulnerabilities. Network attack is a complex and highly procedural work. The whole process of a hacker launching a network attack can generally be divided into three stages: the preparation stage of the attack, the implementation stage of the attack, and the post-processing stage of the attack, as shown in Figure 6-30. In the preparation stage of the attack, the hacker determines the attack target, understands the target's network structure, collects the target system information, and analyzes and detects the security vulnerabilities or weaknesses of the target system. When hackers collect enough information about the target system and detect the security weaknesses of the target system, they will take different means to launch attacks according to different network structures and system conditions. After successfully invading the target system and gaining control, hackers generally need to clear system logs and other records and leave a back door in order not to be discovered by the administrator and then retain and consolidate their control over the system for a long time. Then, hackers steal the information of the intruded system or delete the data in the system, and may even use the system to launch new attacks. In order to improve the success rate of attacks, hackers generally only choose specific systems as the target of attacks. These systems generally have security vulnerabilities, or the maintenance measures are incomplete and lack of a good security system, including routers, databases, Web servers, FTP servers, and protocol related services, such as DNS. The purpose of hacker launching network attack mainly includes: eavesdropping, tampering, destroying or forging the information transmitted on the network; Destroy the network performance and make the network system unable to operate normally. Let's take a look at an example - attacks on the Internet cause network security fears. On October 21, 2002, hackers attacked the core server of the Internet. Security experts agreed that this was a well prepared attack. The 13 root servers, which are critical to the naming system of the Internet, are full of messages sent by hackers. Hackers expect to use traffic to completely defeat these servers. This attack is essentially global - because these root servers are distributed around the world. These hackers are not aimed at a specific Web site or service provider, but to attack the Internet itself. Because the root server is a global system running domain names and Internet addresses, they are responsible for matching Internet addresses with user requests. Observers called the attack the largest and most targeted attack in history. The purpose of this attack is to destroy the Internet all over the world, which is believed by investigators. In this sense, this attack is unsuccessful. Although the services of 9 of the 13 root servers were damaged, most Internet users did not feel that the Internet response time was different from the normal situation during the attack lasting for one hour. The fact that an attacker cannot stop the Internet is proof of the robustness of the Internet. In addition, many network security experts believe that a distributed attack of this scale, if it lasts a little longer, may cause catastrophic consequences. If this attack continues, Internet services may deny millions of users. It is common to try to defeat the server. Hackers often try to destroy the servers used by companies, schools and governments to maintain Web sites by sending useless information that overload servers. Therefore, the security experts of the government and the company constantly detect and stop hackers around the clock, trying to stop them before causing damage. Although there is security protection, sometimes the attack is very fierce, even defeating Amazon com、 Yahoo! And eBay. In addition to hacker attacks, computer viruses are also an important factor threatening network and computer security. Computer virus is a self replicating program, which will disturb the normal operation of the computer or destroy the useful data of the computer. When the computer is connected to the network, the harm of computer viruses is even greater, and strict precautions must be taken. At present, the prevailing practice is to focus on prevention. In order to do a good job in prevention, necessary anti virus and anti-virus systems should be equipped. 2. Safety measures In order to ensure the security of network and information, necessary security measures and technologies must be taken. (1) Virus protection software Although the emergence of computer viruses is less than 30 years ago, there are millions of known computer viruses and they are still increasing. Some viruses have special names, such as Red Code, Melissa, Christmas virus, Panda Burns Incense, etc. In order to protect the system from virus infection, virus protection software should be purchased to scan the computer memory and disk to detect virus programs. The two main virus detection methods are scanning and interception. The scanner searches the memory to detect a virus. Most programs will warn users when they detect a virus, and then destroy the virus and try to repair the data according to the user's instructions. The detection program works in the background to monitor and process various activities of the computer and notify the user when the virus attempts to infect the system. (2) Digital signature Digital signature relies on a mathematical coding scheme to verify the identity of message sender or document signer. In e-commerce, a perfect digital signature has the functions that the signatory cannot deny, others cannot forge, and can verify the authenticity in front of a notary. The Electronic Signatures in Global and National Commerce Act, commonly known as the E-Signature Bill, came into force in 2000. It stipulates that digital signatures have the same legal effect as traditional signatures written in ink on paper. The law does not stipulate specific digital signature technology, so IT manufacturers and service providers are studying various methods to verify a person's legal identity, including the use of personal smart cards, PDA encryption devices and biometric verification methods. This law only applies to electronic affairs in the United States. It encourages companies to develop procedures for the use of electronic signatures to speed up daily business activities and reduce the cost of mailing and processing paper contracts and other business and legal documents. (3) Encryption If the concern is to protect the data from interception and illegal use, the most effective security measure is to encrypt the data. Encryption technology uses a mathematical algorithm to transform data into an encryption form called ciphertext, in which the key is an important element. The complexity of the key is a factor in determining the security of the ciphertext. The three widely used encryption methods are public key infrastructure, PGP and virtual private network.- The Public Key Infrastructure (PKI) uses the same algorithm to create two keys: the public key and the private key. The certification authority issues and manages the security certificate and public key for message encryption. The private key is only provided to the requester and is not shared with anyone. On the contrary, the public key is placed in a directory that can be searched by all parties. Therefore, the sender who wants to transmit encrypted messages searches the directory of digital certificates to find the public key of the receiver, and uses the public key to encrypt the information. When the receiver receives the encrypted message, it decrypts it with the private key.
- PGP (Pretty Good Privacy) is a mail encryption software based on RSA public key encryption system. It can be used to encrypt the message to prevent unauthorized persons from reading it. It can also add digital signatures to the message so that the recipient can confirm the sender of the message and be sure that the message has not been tampered with. It can provide a secure way of communication, and does not need any confidential channel to transfer the key in advance.
- Virtual Private Network (VPN) is a method of using public telecommunications infrastructure to provide secure communication between remote personal or client computers and enterprise networks. VPN works through shared public infrastructure, but maintains privacy through security procedures and tunnel protocols. These protocols send data through a tunnel, encrypt the data at the sending end, decrypt it at the receiving end, and only correctly encrypted data can enter the tunnel.
(4) Firewall Firewall is considered as an indispensable peripheral defense system for access via data communication channels (whether wired or wireless). The firewall is usually a special software located on the gateway server of the network to protect users of the private network. If the firewall determines that messages sent by users on other networks may contain harmful programs or data, it will prevent these messages from entering. Some important information systems, such as those involving national and defense secrets, usually need to set up hardware firewalls. (5) Proxy server Proxy servers are usually used to ensure the security of Internet applications. The proxy server acts as a medium between the user's computer and the Internet, separating an internal network from an external network. It is often used with firewalls and often contains a cache to store previously downloaded Web pages.
Source Statement: This article is original or edited by Shangpin China's editors. If it needs to be reproduced, please indicate that it is from Shangpin China. The above contents (including pictures and words) are from the Internet. If there is any infringement, please contact us in time (010-60259772).