-
simplified Chinese character -
Simplified Chinese English
Shangpin China Joins Hands with Beisheng Internet to Create a New Chapter in Website Construction
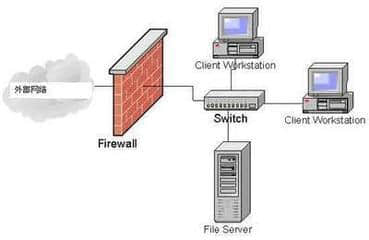
Limitations of firewall
Station building process
-
Website requirements -
Website planning scheme -
Page design style -
Confirm delivery for use -
Data entry optimization -
Program design and development -
Follow up service -
contact number 010-60259772
Hot tags
-
Website construction -
Food website construction -
WeChat applet development -
Applet development -
Wuxi website construction -
Website construction of research institute -
Shenyang website construction -
Langfang website construction -
Zhengzhou website construction -
Construction of wedding photography website -
Mobile terminal website construction -
University website production -
Tianjin website construction -
Education website construction -
Brand website construction -
Government website construction -
Beijing website construction -
Website Design -
Website production
Latest articles
-

Website construction scheme: Fresh makeup aesthetics website Type: website construction 2025-03-13 -

Enterprise website construction plan: create a new business card for the network and open the digital future Type: website construction 2025-03-11 -

High end website production solution Type: website construction 2025-02-18
Recommended News
-
How to operate and maintain enterprise websites? How to operate and maintain general corporate websites? In the case of limited staff and financial resources, how to 2019-08-22 -
How to optimize long tail keywords Long tail keywords cannot be ignored Website production company Shangpin China: Long tail keywords can bring traffic and popularity to the website 2013-04-23 -
Classification of Computer Economic Simulation Technology The simulation model can be divided into deterministic model and stochastic model. Now, we can use the economic model on this basis 2016-03-31 -
How to improve the user experience of enterprise websites Architecture is the skeleton of a website. The architecture of a website is very important 2013-05-06 -
What are the benefits of website exchange of friendship links? Select the category of the link station Website construction needs to exchange links selectively, only the same type 2021-12-11 -
Some basic principles of website production In today's Internet era, websites have become an important platform for enterprises to show their image and promote products and services 2024-10-25
Make an appointment with a professional consultant to communicate!
Disclaimer



