-
simplified Chinese character -
Simplified Chinese English
Shangpin China Joins Hands with Beisheng Internet to Create a New Chapter in Website Construction
Design principles of firewall
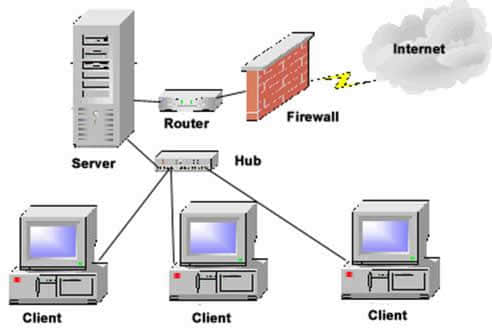
Station building process
-
Website requirements -
Website planning scheme -
Page design style -
Confirm delivery for use -
Data entry optimization -
Program design and development -
Follow up service -
contact number 010-60259772
Hot tags
-
Website construction -
Food website construction -
WeChat applet development -
Applet development -
Wuxi website construction -
Website construction of research institute -
Shenyang website construction -
Langfang website construction -
Zhengzhou website construction -
Construction of wedding photography website -
Mobile terminal website construction -
University website production -
Tianjin website construction -
Education website construction -
Brand website construction -
Government website construction -
Beijing website construction -
Website Design -
Website production
Latest articles
-

Website construction scheme: Fresh makeup aesthetics website Type: website construction 2025-03-13 -

Enterprise website construction plan: create a new business card for the network and open the digital future Type: website construction 2025-03-11 -

High end website production solution Type: website construction 2025-02-18
Recommended News
-
The operation and profit idea of "supporting the station with the station" is the foundation of website development Beijing Website Construction Company Shangpin China: Website is a term that touches the hearts of countless webmasters, and webmasters will 2013-03-19 -
Main services of the Internet The Internet is a huge Internet system, website design, its resources are very rich, including 2015-06-26 -
Explain the steps and principles of external chain It is not necessary to list all the choices here. There are many addresses in the outer chain. It can be specialized in several categories 2013-06-15 -
Simple website design will be the trend in the future The biggest charm of marketing website construction lies in marketing, while marketing customers are a profound knowledge 2015-04-30 -
What is the part of website optimization that is easy to be ignored in Beijing website construction? Don't mention the ranking of keywords on the website today. Today, let's talk about what is easy to ignore in the SEO optimization process 2022-09-27 -
On site optimization to improve ranking skills The website META optimization description and keyword are three parts 2013-06-22
Make an appointment with a professional consultant to communicate!
Disclaimer



